Information Security / Cybersecurity
Wistron's Information Security / Cybersecurity management mission is to “build a resilient, secure, and trustworthy enterprise.” The Company has established an Information Security Policy as its core guiding principle and is fully committed to driving digital transformation through the implementation of comprehensive information security management mechanisms. We focus on ensuring the integrity and availability of information processing and protecting the security of information systems, equipment, and networks. Through regular information security/cybersecurity drills and employee training programs, Wistron strives to build a comprehensive protection network to safeguard its information assets from potential threats.
ISO 20000
IT Service Management System
In February 2018, Wistron obtained the information service management system international standard ISO/IEC 20000-1:2011 certification. The Company seeks excellent IT service management and internationally recognized IT management standards to ensure that our information technology infrastructure library (ITIL) operations meet the required the standards. Wistron completed the certification for the updated ISO 20000-1: 2018 in January 2021 and continues to optimize the IT service management system and related procedures to continue to strengthen data governance.The current certificate is vertified by SGS and valid until February 22, 2027.
ISO/IEC 20000 changes the method for implementing internal IT services or outsourcing IT services. The benefits are as follows:
- Meet best-practice standards for international IT management
- IT services support the fulfillment of company goals
- Integrate personnel, processes, and technologies to support company goals
- Use control measures for evaluation and to maintain consistent service quality
- Compatibility between ISO/IEC 20000 and Information Technology Infrastructure Library (ITIL) supports continuous improvement
ISO 27001
Information Security Management System
Wistron obtained the information security management system international standard ISO/IEC 27001:2013 certification in August 2017 and implemented the “Plan-Do-Check-Act” (PDCA) cycle according to the standards. The Company conducts at least one internal self-audit and one audit by an impartial third party every year. To ensure the Company's implementation of ISO 27001 management mechanisms, the Company executes re-certifications every three years to maintain the validity of the ISO 27001 certification.The current certificate is vertified by SGS and valid until August 22, 2026.
- Regarding the critical infrastructure and the important information systems required for continuous operations, Wistron's headquarters (Neihu and Xizhi office areas), Hsinchu plant and all overseas manufacturing plants have successively obtained ISO/IEC 27001: 2013 verification. Also, we achieved the verification of ISO/IEC 27001: 2013 the international standard for information security management for all manufacturing plants in 2022 with a coverage rate of 100%.
- In August 2024, Wistron’s headquarters (Neihu and Xizhi offices), Hsinchu site, and all overseas manufacturing sites completed the full transition to the ISO/IEC 27001:2022 certification. Coverage rate 100%. Note: Sites sharing a data center do not have independent certification.
Note: Sites sharing a data center do not have independent certification.
Information Security Policy and Organization
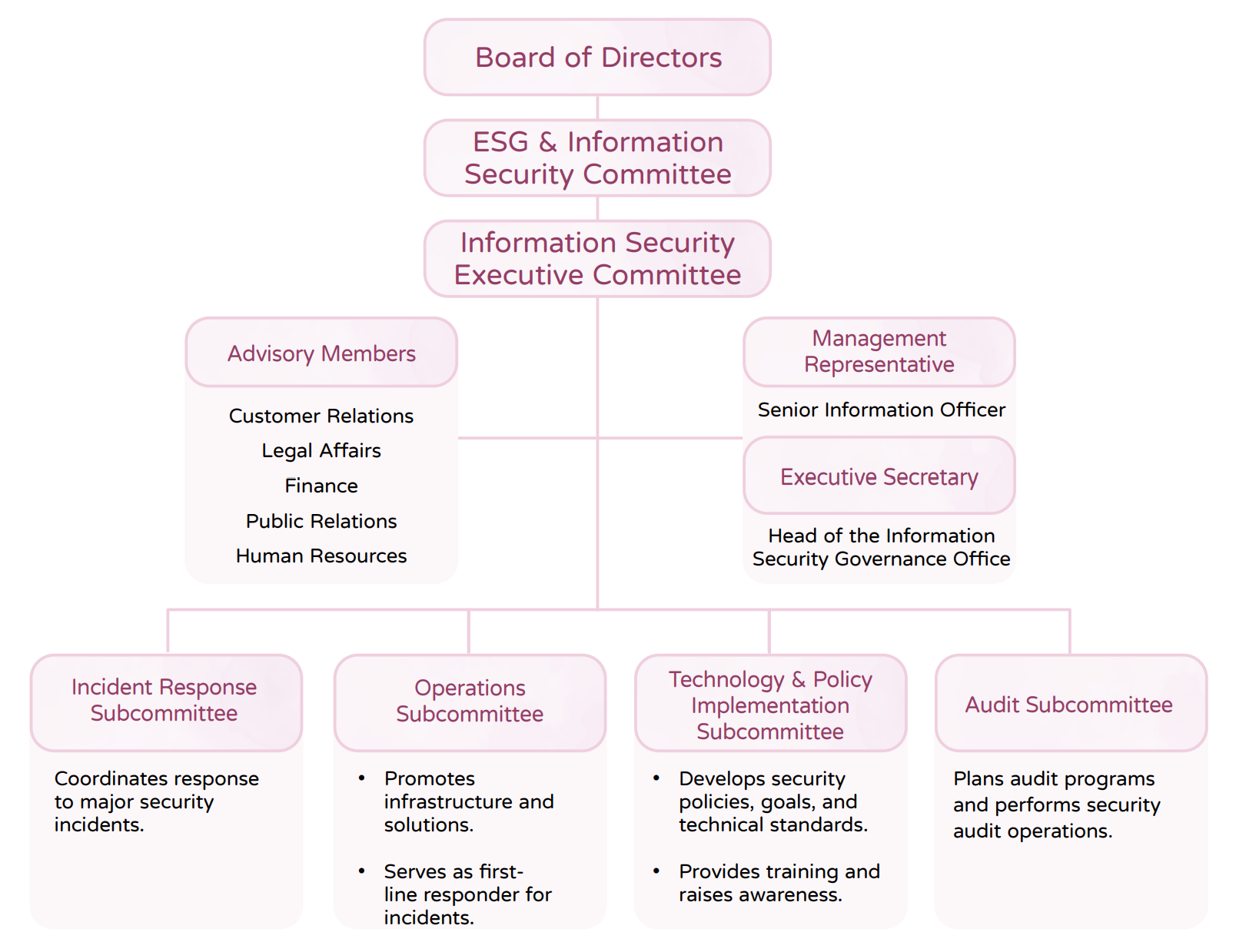
To effectively implement the ISO/IEC 27001 Information Security Management System, Wistron focuses on integrating procedural systems, ensuring regulatory compliance, providing personnel training, and utilizing technological applications to enhance the protection of data, information systems, equipment, and network communications. Through effective management, Wistron aims to reduce the risks of information asset theft, misuse, leakage, tampering, or destruction due to human error, malicious actions, or natural disasters, thereby fulfilling its commitments to shareholders and customers, and ensuring business continuity and operational stability. To strengthen the company’s long-term competitiveness and enhance information security governance, Wistron’s Board of Directors approved the renaming of the “ESG Committee” to the “ESG and Information Security Committee” on April 2, 2025. Under this committee, an Information Security Executive Committee was established, comprising the President & CEO, Chief Operating Officer & CTO, and Chief Digital & Information Security Officer, underscoring the Company’s commitment to cybersecurity oversight. This committee supervises the implementation of Wistron's information security systems, technical standards, and operational practices. Wistron appointed the Vice President of Information Technology as the Management Representative, and the Head of the Information Security Governance Office as the Executive Secretary, to coordinate information security/cybersecurity affairs across the company. Wistron has established an Information Security/Cybersecurity Policy to serve as the foundation for protecting the information assets of employees, customers, suppliers, and business operations, ensuring the Company’s sustainable development.
Information Security/Cybersecurity Policy
To protect Wistron’s information, products and services, avoid unauthorized access, modification, use and disclosure, as well as losses caused by natural disasters, and provide complete and available information in a timely manner, Wistron is committed to information security/cybersecurity management to ensure the confidentiality, integrity, and availability of important information property and comply with the requirements of relevant laws and regulations, thereby gaining customer trust, meeting commitments to shareholders, and ensuring uninterrupted business operations.
Information Security Executive Committee Structure
The Information Security Executive Committee (formerly the Information Security Committee) convenes on a quarterly basis. Ad hoc meetings may be convened when necessary, and members of the teams are required to attend. The meeting agenda includes information security incident reports, the report from each team on the implementation of their affairs, issues that require the cooperation of different units, other related suggestions, and extemporaneous motions. A total of four meetings were held by the Information Security Committee in 2024, and the management representative reported the information security/cybersecurity implementation status to the Board in December.
Information Security Protection Strategy
To address the rapidly changing internal and external environment, Wistron has established a dedicated information security organization responsible for the planning, implementation, and risk management of information security/cybersecurity policies. Focusing on three major areas—Information Technology (IT) security, Operational Technology (OT) security, and cloud security—Wistron continuously enhances system protection, data security, and operational stability through a robust internal cybersecurity framework. Wistron also actively participates in cybersecurity intelligence-sharing platforms, including the High-Tech Cyber Security Alliance and the Taiwan Computer Emergency Response Team/Coordination Center (TWCERT/ CC), to obtain the latest security alerts, threat intelligence, and vulnerability information, enabling the company to quickly identify potential risks and deploy preventive measures in advance.
Wistron utilizes the Cybersecurity Framework (CSF) stipulated by the National Institute of Standards and Technology (NIST). We evaluate the overall information security maturity and plan development blueprints for information security. We determine the priority of each matter and allocate resources accordingly, making rolling adjustments to continually strengthen and improve our systems. The framework provides the five key functions of identification, protection, detection, adaptation, and recovery. The functions include management measures for every stage of an attack against the Company, that is, pre-incident (identification and protection), during the incident (detection and adaptation), and post-incident (recovery). In the future, information security/cybersecurity is based on the Zero Trust Architecture (ZTA), which requires that every user, device, and application must undergo identity authentication and obtain authorization before accessing network systems or assets. The scope of information security/cybersecurity protection will be further extended to cloud cybersecurity (including public cloud and private cloud) and operational technology (OT) cybersecurity. We will also introduce related cybersecurity standards and assessment models, such as Cybersecurity Capability Maturity Model (C2M2), CSA Consensus Assessments Initiative Questionnaire (CSA CAIQ), and ISO/IEC 62443. As such, we assure that our overall cloud cybersecurity and operational technology cybersecurity defense capabilities will be further strengthened in the future. In response to emerging risks associated with generative AI, Wistron has enhanced its AI governance mechanisms by integrating cybersecurity governance frameworks and protection measures. Guided by the vision of Sustainability through Innovation, the Company continues to advance digital transformation, striving to build a resilient, secure, and trustworthy enterprise.
Information Security/Cybersecurity Operation Measures:
- Identify stakeholder groups associated with the information security management system and regularly verify the needs of stakeholder groups for the information security management system (including customers' demands for information security).
- Execute social engineering drills and information security training for employees to fully increase employees' information security awareness.
- Establish comprehensive and clear operating procedures to institutionalize the operations of the information security management system.
- Perform regular risk assessments to identify high risk items and invest appropriate resources to reduce or transfer risks.
- Use tools and technologies to achieve timely and effective identification, protection, detection, response, and recovery.
- Establish operating procedures for response and recovery in the event of information security anomalies with the aim of rapid isolation of information security incidents, elimination of threats, and reduction of the scope and extent of impact.
- Perform regular disaster recovery exercises for key applications to ensure their effectiveness.
- Perform regular annual internal and external audits each year to review the entire management system and ensure normal operation and continuous improvement.
- Continuously pay attention to new information security development and technologies and update defense or management practices to effectively block new forms of information security threats and reduce risks for operations.
Information Security/Cybersecurity Management Plan
Information Security Management and Audit Mechanisms
In order to protect the Company’s intellectual property (including confidential information) and confidential customer information, Wistron has conducted multiple self-assessments and external third-party audits annually since 2017. For self-evaluations, we follow the NIST Cybersecurity Framework (CSF) and ISO/IEC 27001 standards. For external third-party audits, we comply with ISO/IEC 27001 standards and our customers’ information security requirements. These audit activities aim to ensure the effectiveness and continuous improvement of information security measures, while also strengthening internal information protection mechanisms. To support business unit development and enhance industrial control system (ICS) security, Wistron’s headquarters and Kunshan site in China successfully obtained certifications for the international automotive cybersecurity standard ISO/IEC 21434 verified by TUV (TÜV Rheinland) and the European automotive cybersecurity standard TISAX certified by SGS, in 2024, further advancing the Company’s information security/cybersecurity capabilities in the automotive sector.
Wistron actively reinforces internal control mechanisms through self-assessments conducted by operational units, in conjunction with audits by the Information Security Governance Office and the Audit Department, as part of a three-line defense. This ensures the effective implementation and continuous improvement of information security measures across all sites. In July and December 2024, operational units conducted comprehensive self-assessments using the Internal Control System (ICS), reviewing the computerized information system cycle and 11 sub-cycles. The review encompassed information systems and security policies, organizational structures, and the effectiveness of control measures in design and implementation. In June, the Information Security Governance Office completed an internal audit in alignment with the ISO/IEC 27001 transition, with no major nonconformities identified. In May, the Audit Office conducted a review in accordance with the “Internal Audit Implementation Guidelines,” focusing on information systems and security risks. The audit assessed the appropriateness of internal control systems, the implementation of general operating procedures, and specific audit projects. No major internal control deficiencies were found. In 2023 and 2024, Wistron received the Taiwan Corporate Sustainability Award (TCSA) Information Security Leadership Award for two consecutive years. In 2024, Wistron won the Information Security Governance Excellence Award at the IT Awards of Taiwan Inspection Technology Corporation (SGS), demonstrating the Company’s exemplary role and leadership position in information security management across the industrtry.
Supplier Chain Information Security Risk Management
In terms of supplier information security management, Wistron follows the Information Vendor Risk Management (VRM) process to classify and tier vendors, assessing their information security management life cycle from the perspectives of security, risk, and privacy. The life cycle covers the procurement phase (tier assessment, risk score assessment, contract), ongoing third-party risk management (risk score assessment and remediation), and the eventual offboarding. A total of 275 vendors were identified in 2024. Vendors were classified into tiers based on risk factors such as the importance of the services they provide, their relevance to customers and revenue, and their ability to directly access the Company’s network environment and confidential information. Vendors are classified into three tiers, with Tier 1 and Tier 2 vendors—those with higher risk levels—required to meet Wistron’s information security assessment standards based on their respective levels of risk tolerance. Our risk score assessment identified nine vendors that comply with Wistron’s information security standards.
Strengthen Employee Information Security Awareness
To strengthen employee awareness of information security/cybersecurity, Wistron actively promotes cybersecurity education and training programs. Through a combination of online and in-person courses, the Company covers topics such as general information security awareness, the “Information Security/Cybersecurity Essentials” series, and phishing email identification and prevention, helping employees understand fundamental security concepts and practical applications. In 2024, a total of 24,337 training completions were recorded, amounting to 21,346 training hours. Additionally, disciplinary actions were taken for 46 incidents involving violations of information security/ cybersecurity policies, reinforcing the importance of cybersecurity.
To enhance overall information security/cybersecurity management and respond to increasingly complex cybersecurity challenges, Wistron launched the Technical Competency Model (TCM) in 2021 to ensure that its cybersecurity personnel possess the necessary skills and knowledge. Based on workforce assessments, the program defines four key roles—Security Governance, Security Engineering, Security Analysis, and Secure Software Development—each with five competency levels. Annual capability assessments are conducted to inform targeted development and advancement plans, ensuring that talent continues to evolve in line with advancements in the cybersecurity field. By 2024, a total of 89 employees—including 26 dedicated cybersecurity personnel— had joined the program, demonstrating Wistron’s strong commitment and continued investment in cybersecurity talent development.
To further enhance the professional capabilities of its cybersecurity team, Wistron encourages employees to participate in security conferences and related training programs. In 2024, the information security/ cybersecurity team completed 1,599 training sessions, totaling 7,850 training hours. These included six core cybersecurity courses, five secure software development courses, and various international certification programs, such as EC-Council CEH (Certified Ethical Hacker), CISSP (Certified Information Systems Security Professional), CISM (Certified Information Security Manager), CISA (Certified Information Systems Auditor), and CompTIA certifications. These programs have not only strengthened the team's technical expertise but also enhanced its ability to address a wide range of cybersecurity threats, thereby improving the company’s overall defense capabilities.The implementation of this program aims to ensure that Wistron remains equipped to meet rapidly evolving cybersecurity challenges, safeguard its information assets, and increase employees’ awareness and responsiveness to information security/cybersecurity risks, maintaining a competitive advantage in the field.
To educate employees on information security/cybersecurity, the Company provides e-Learning resources and holds social engineering exercises every six months on phishing email simulations, reviews of employee information security awareness, and information security education and training. In addition, the Company publishes cybersecurity e-newsletter every month to enhance our employees' awareness and vigilance of cybersecurity. The e-newsletter covers the latest cybersecurity trends and recent major cybersecurity events at home and abroad. To mitigate information security/cybersecurity risks and minimize its potential impacts, employee violations against our Information Security Policy will result in penalties according to the "Implementation Guidelines for Employee Rewards and Penalties" and be factored into their performance evaluations.
- The phishing email click rates for social engineering drills conducted in the last 4 years on all company employees are as follows:
| Measures |
Goal |
2021 |
2022 |
2023 |
2024 |
| Execute social engineering drills every six months |
The social engineering drill email click rate among employees was < 15% |
H1 : 10.8%
H2 : 10.7% |
H1 : 9.3%
H2 : 10.2% |
H1 : 7.4%
H2 : 8.2% |
H1 : 7.8%
H2 : 12.6% |
Vulnerability detection for networks and systems
Apart from monthly internal vulnerability scans, Wistron entrusts a third party professional organization to conduct network and system penetration tests each year to protect the corporate and personal information and prevent losses caused by leaks, theft, destruction, other human factors, or natural disasters. These tests reduce the impact of human factors or natural factors on the Company's operations. The purpose of the tests is to understand and evaluate the status of the organization network environment and system security and verify the current information security protection safety rating and effectiveness to resolve vulnerabilities, improve operations, and strengthen system security.
Since 2021, we introduced red team drills, where external information security teams simulated attacks on the Company and attempted to achieve specified goals without affecting the Company’s operations. The red team drills allow us to comprehensively review our services and networks for any vulnerabilities and human errors in deployment. Moreover, we checked the integrity of identification, protection, detection, and response mechanisms from our information security maintenance and response team.
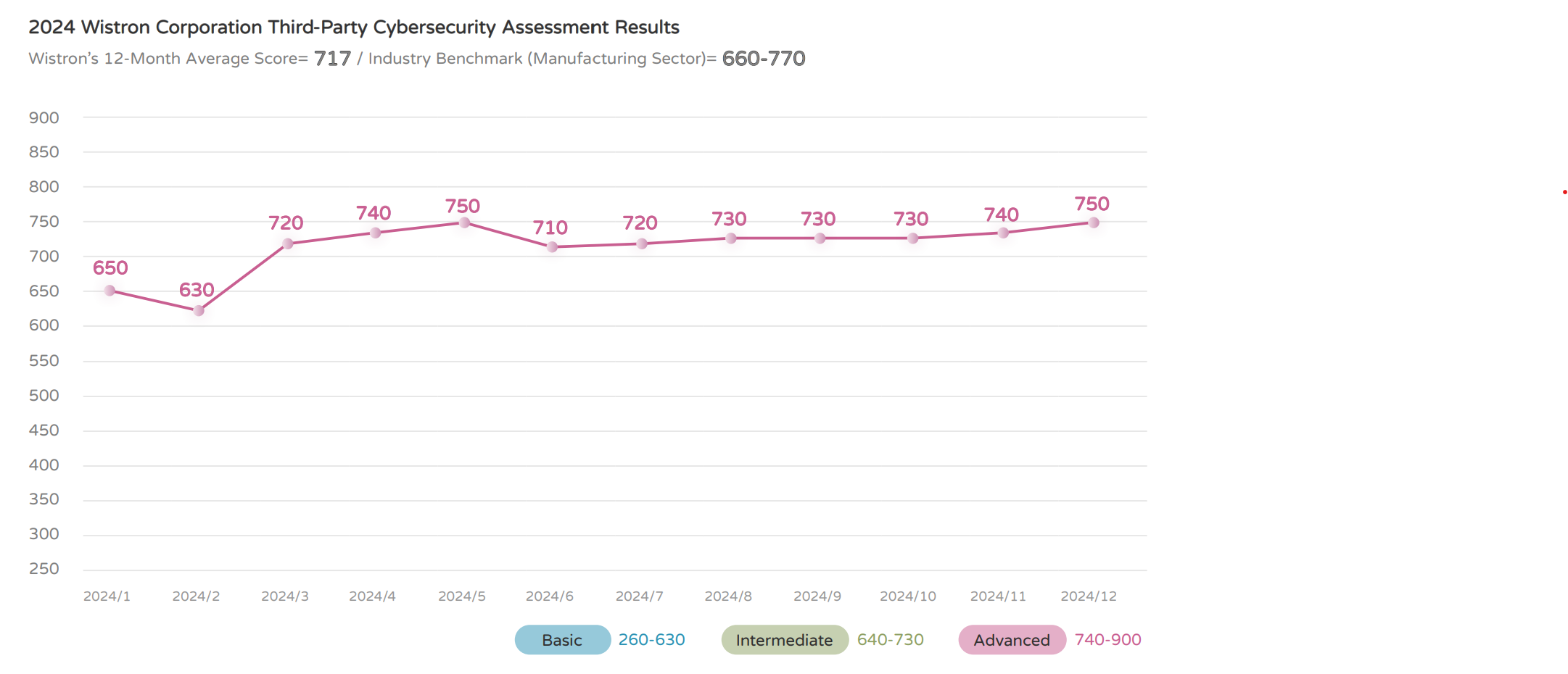
In 2024, Wistron Corporation achieved an average score of 717 in its third-party cybersecurity assessment. External evaluation enabled timely adjustments and reinforcements of network and service vulnerabilities.
Software Development Security
In order to control the security of the software development lifecycle (SDLC) and achieve "shift left" security to thereby reduce the operational costs associated with application security and maintenance, Wistron has adopted the DevSecOps (Development, Security, and Operations) mechanism. This approach enhances collaboration among the development, operations, and information security teams. Additionally, Wistron has adopted the DevSecOps Maturity Model (DOSMM) from the non-profit organization OWASP (Open Web Application Security Project) to assess the overall maturity of software development practices. This ensures that the software released meets predefined information security maturity standards. Furthermore, the incorporation of Software Composition Analysis (SCA) technology into the development workflow enhances the security quality of the software.
Information security alerts and incident management
To ensure the effectiveness of information security/cybersecurity management and enable prompt handling of security incidents, vulnerabilities, or suspicious activities, Wistron has established a comprehensive information security escalation process. This allows employees to immediately report issues and activate response mechanisms upon detection. Employees can report suspicious behavior, vulnerabilities, or security incidents to the responsible personnel through various channels, including internal platforms such as the local IT helpdesk (ext. 11119), reporting systems, or by directly contacting the Information Security team. This process ensures that every security incident receives timely attention and that appropriate response measures are initiated without delay.
To enhance rapid response and continuous protection against security incidents, Wistron has implemented an Advanced Persistent Threat (APT) monitoring mechanism, which plays a critical role in the operations of its Security Operations Center (SOC). The SOC integrates resources from both internal cybersecurity specialists and external experts to conduct 24/7 continuous monitoring and detection of potential security threats. This setup enables comprehensive oversight of the enterprise’s network security posture and related alerts, allowing timely identification and mitigation of threats and preventing the escalation of security incidents.
Regardless of the incident reported by employees or monitored by the system, according to the Wistron Information Security Incident Management Specification, information security incidents are divided into 6 levels, assessed based on the severity of 3 types of accidents, mobilize 3 different levels of response organizations, and also set the timeliness of handling and report update frequency. Each incident response process follows nine steps: initial notification and assessment/classification, escalation, initial containment, analysis, post-analysis containment, eradication, recovery, reporting and post-event experience inheritance,this process ensures the reporting, classification, handling, institutionalized statistics and tracking, so as to quickly report and deal with the occurrence of information security incidents, and reply in the shortest possible time to ensure the normal operation of various businesses.
Business Continuity Management and Disaster Recovery Drills
To ensure the continuity of operations and critical business functions while minimizing the impact of major disaster events on key information systems, Wistron has established a comprehensive Information Security Business Continuity Plan. This plan is designed to address various unexpected situations and ensure the rapid and effective recovery of critical application systems in the event of information security/cybersecurity incidents or natural disasters, thereby preventing operational disruptions. According to the plan, Wistron conducts at least one test every six months through tabletop exercises simulating the Business Continuity Plan or Cybersecurity Incident Response Plan. These drills simulate potential cyber threats or disaster scenarios to verify the feasibility of the response plan. Through these regular tests, Wistron is able to effectively identify potential vulnerabilities, enhance response capabilities, and reduce the risk of operational disruption. In addition to drills, Wistron conducts at least one annual backup data restoration test to verify the readability of backup data, the availability of storage media, and the feasibility of recovery procedures for critical assets. These tests ensure that all data can be successfully restored within the designated timeframe, thereby reducing system recovery time and safeguarding business continuity.
The global IT center also selected 18.95% of backup storage media for seven key functional systems and databases in 2024. Recovery testing was successfully completed for the backup data. The annual global computer center disaster recovery drills revealed that the maximum tolerable data loss time during disasters (Recovery Point Objective, RPO) is 0.6 hours. After a disaster occurs, the maximum tolerable information service recovery time (Recovery Time Objective, RTO) is 19.22 hours. The results of the drills in the last four years have met the Company’s targets, and details can be found in the table below :
| Strategy |
Goal |
2021 |
2022 |
2023 |
2024 |
| Disaster recovery simulations are conducted for key applications and systems every year to ensure continued operations and the uninterrupted provision of Company services. |
RPO of SC2
Services<=4 hours
RTO of SC2
Services<=24 hours |
RPO=0.8 hour
RTO=22.0 hours
|
RPO=0.9 hour
RTO=18.83 hours |
RPO=1.0 hour
RTO=22.11 hours |
RPO=0.6 hour
RTO=19.22 hours |
- RPO: Recovery Point Objective (the maximum tolerable data loss time during disasters)
- RTO: Recovery Point Objective (the maximum tolerable information service recovery time after a disaster occurs)
In addition to disaster recovery drills for information systems, Wistron also organizes information security incident response drills every year. Invite members of the Information Security Execution Committee to simulate information security incidents and conduct scenario drills to ensure that the Company has sufficient information security protection and control mechanisms, emergency notification and response capabilities in the event of a hacker attack, thereby enhancing overall information security resilience.
Information Security Insurance Mitigates Information Security Risks
Since 2021, Wistron purchased global information security insurance policies as a group. Apart from mitigating risks, we also hope to further receive the help and resources of external information security experts through the international insurance market, leveraging their preventative solutions to strengthen existing information security/cybersecurity measures so that we may respond to growing information security threats and achieve corporate sustainable management.
Information security incidents in the most recent 4 years
In 2024, Wistron experienced two major information security incidents. The first occurred on March 25, when a fire at the Hsinchu site in Taiwan caused a power outage in the server room. The second took place on October 4, when the Company’s official website was targeted by a Distributed Denial of Service (DDoS) attack. In response to the cyberattack, defense mechanisms were immediately activated. There was no significant impact on business operations, and no leakage of personal data or internal documents was identified.
| Number of information security violations and fines/year |
2021 |
2022 |
2023 |
2024 |
| Number of information security or network security violations |
0 |
0 |
0 |
2 |
| Data leak incidents (number of cases) |
0 |
0 |
0 |
0 |
| Number of information security violations that involve customer information |
0 |
0 |
0 |
0 |
| Number of customers and employees affected by the data leak (number of people) |
0 |
0 |
0 |
0 |
| Amount of fines for information security or network security related incidents (NTD) |
0 |
0 |
0 |
0 |
Privacy Protection
To implement personal data protection and management, Wistron formulated its Privacy Policy with reference to the laws and regulations of the jurisdictions in which it operates, and in alignment with the relevant requirements of the European Union’s General Data Protection Regulation (GDPR) as the highest guiding principle for privacy protection. The policy applies to all personnel of Wistron, Wistron’s subsidiaries and joint ventures over which Wistron has significant influence, as well as suppliers, contractors, external consultants, and other third-party partners. The policy outlines clear specifications and requirements for the use and protection of personal data, as well as related matters. All internal personnel and third-party partners are required to strictly adhere to the policy to ensure the security of personal data and protect the rights and interests of relevant stakeholders.

Ensuring the confidentiality of customer information and upholding the principle of integrity
Wistron incorporates privacy and personal data protection into its Enterprise Risk Management systems and promotes related management actions in accordance with the “Risk Management Policy and Procedures” to reduce operational risks and potential impacts. In addition, the Internal Control Department conducts an internal audit project every six months through the Internal Control System (ICS) to review the collection, processing, and transfer of personal data, ensuring that all operations comply with local regulations and internal Code of Conduct.
Wistron has established complaint channels for privacy-related incidents. If anyone discovers or suspects a violation of privacy rights or a breach of the policy, they may report the issue through the Privacy Protection Hotline at (02) 6616-9999 ext. 25740 or via email at ethic@wistron.com. We adopt a zero-tolerance policy toward privacy violations. Any individual found in breach of this policy will be subject to disciplinary action in accordance with the relevant provisions of the Code of Conduct, ensuring the rigor of personal data management procedures.
To strengthen privacy awareness, Wistron promotes its Privacy Policy and emphasizes its importance across global operating sites through internal electronic bulletin boards, emails, physical notices, and other communication channels. In addition, starting from the second quarter of 2024, Wistron launched the “Privacy and Data Protection Awareness” training for all employees across 25 global operating sites in 10 languages. A total of 17,886 employees completed the training, achieving a 100% coverage rate and further enhancing employee awareness and compliance with personal data management practices.
“Strictly guarding customer confidentiality and upholding the principle of integrity” is Wistron’s core commitment to customer privacy. We strictly adhere to our Privacy Policy and ensure that customer data is never used for secondary purposes (0%), safeguarding the confidentiality of all information. From 2021 to 2024, Wistron has not received any privacy-related complaints or penalties from regulatory authorities or external parties, demonstrating our rigorous management and consistent implementation of personal data protection practices.
Privacy protection hotline
+886-2-6616-9999#25740
Privacy protection email
ethic@wistron.com